I am very new to the CTF game, and when partaking in a recent CTF, I had a lot of trouble with password cracking. I could not find much help online. With this guide, I’m trying to make this process less painful for people in a similar situation.
This is what we knew about the password:
Our password policy for the domain is CTF{[ROCKYOU]_[ROCKYOU]!} where at [ROCKYOU] you are allowed to pick any word from the rockyou.txt list.
OHaalstra@deloitteNL.
My first attempt to crack the hash looked something like this:
┌──(bballiu㉿DESKTOP-DIL5EI2)-[~]
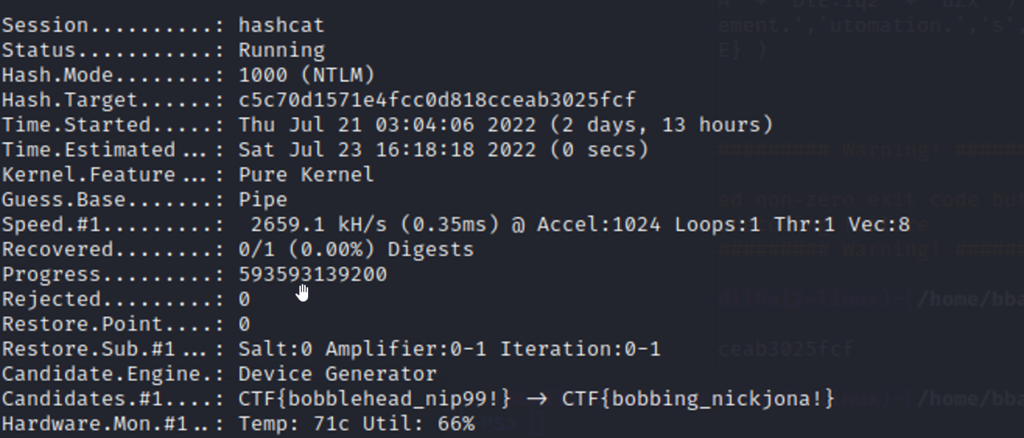
└─$ sudo john --format=nt ntlm.txt -w:rockyou.txt --mask=CTF{?w_?w\!}People with more experience in password cracking might spot the apparent mistake immediately. I was surprised to see john finish that quickly.
Using default input encoding: UTF-8
Loaded two password hashes with no different salts (NT [MD4 512/512 AVX512BW 16x3])
Warning: no OpenMP support for this hash type, consider --fork=8
Press 'q' or Ctrl-C to abort, almost any other key for status
0g 0:00:00:01 DONE (2022-07-20 11:07) 0g/s 4938Kp/s 4938Kc/s 9877KC/s CTF{luvcaleb10_luvcaleb10!}..CTF{luv_luv!}
Session completed.No successful guess. This method uses the same word from the dictionary with every cycle. This was an operator error.
My second attempt was to use the combinator attack within hashcat.
┌──(bballiu㉿DESKTOP-DIL5EI2)-[~]
└─$ sudo hashcat -m 1000 -a 1 ntlm.txt rockyou.txt rockyou.txtIf you wish to add rules to either the left or right dictionary or both at once, you can use the -j or -k commands.
-j, --rule-left=RULE Single rule applied to each word on the left dictionary -k, --rule-right=RULE Single rule applied to each word on the right dictionary
The syntax is a little funky to me, but after some digging around I was able to come up with a solution.
The solution
┌──(bballiu㉿DESKTOP-DIL5EI2)-[~]
└─$ hashcat -a 1 -m 1000 ntlm.txt rockyou.txt rockyou.txt -j '^{^F^T^C' -k '^_$!$}' -OUsing the ‘-O’ Allowed me to crack at over 500 MH/s instead of 20.000kH/s on my Integrated Graphics Card on the 11th Gen Intel(R) Core(TM) i5-1145G7
By running this command, we finally got what we wanted: the flag. The password ended up being: CTF{city123_unlocked!}
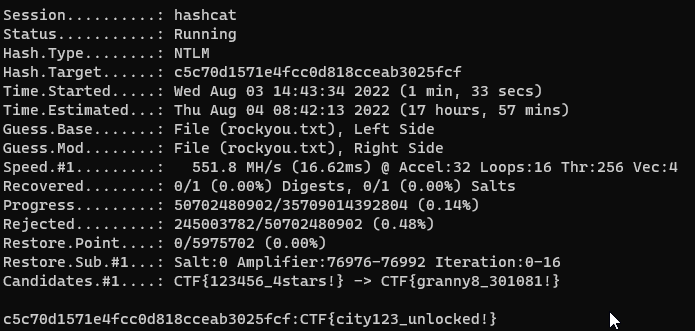
A failed attempt of mine (using hashcat + awk for format + stdin hashcat again): look at the speed difference! Always do your research kids.